What context for fraud?
Situation in France
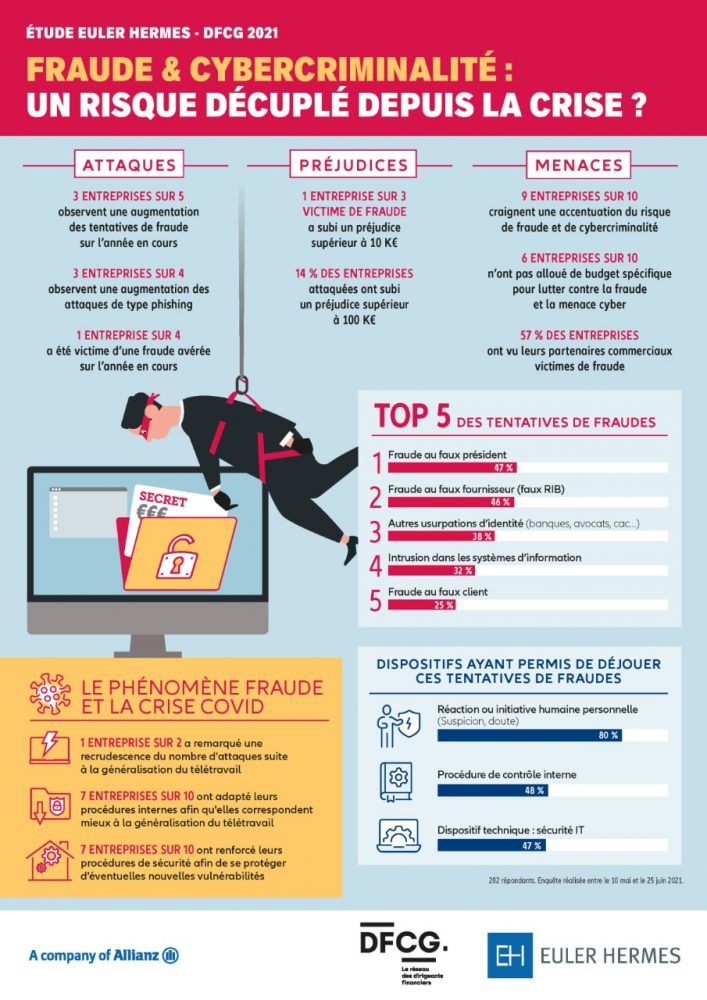
The results of the DFCG 2020 barometer show that identity theft is the most popular technique among fraudsters. Among its various forms, fake supplier fraud is still the most practiced (48% of respondents). It is followed by fake president fraud which has increased significantly (38%), other identity theft (banks, lawyers, auditors - 31%) and fake customer fraud (24%).
Fraud in figures
- 2 out of 3 companies experienced at least one fraud attempt in 2021, and 1 in 5 companies experienced more than 5 attacks
- 33% of the companies that have been victims of fraud have suffered a loss of more than 10,000 euros. 14% have suffered a loss of more than 100,000 euros
- Nearly one in two companies has noticed an increase in attacks as a result of widespread telecommuting (Covid-19)
The different types of fraud in B2B
False supplier fraud
False supplier fraud is the most common technique used by cybercriminals in the last three years. According to the latest study published in 2020 by Euler Hermes and the DFCG, false supplier fraud represents almost half of the frauds represented. This type of fraud consists of impersonating a company's supplier in order to obtain payment of one or more invoices. While the technique may seem crude, it is nonetheless widespread and widely used by fraudsters. Since 2017, it has been the favorite fraud of cybercriminals.
Fake President Fraud
The so-called "President's Scam" has come to the fore in recent years and continues to plague all types of businesses. It is based on social engineering which consists of fraudulently obtaining information for the purpose of fraud.
There have been many cases of fraud against the president in France in recent years. It consists in usurping the identity of a client to demand from an employee an important transfer, generally in a confidential and urgent way.
Fake customer fraud
The fraudulent customer takes different forms. Indeed, it aims at better extorting funds or goods from companies by deception. A fake customer is a fraudster who impersonates a customer or supplier. Fraud aims to misappropriate funds or goods from a company, by reporting a change of address, a change of bank details, or by claiming the return of funds paid after the signing of a quote.
Ransomware
Ransomware attacks have become more and more prevalent in recent years. The current context generates a massive digitalization for institutions and companies, thus increasing the opportunities for hackers. Although they are reluctant to finance cybercrime, some groups still choose to give in to the blackmail of hackers.
#Ransomware- Your data is being held hostage! 💰
- ANSSI (@ANSSI_EN) January 26, 2018
A #infographic to understand and protect yourself from these attacks with strong nuisance capabilities, for individuals as well as for companies
➡️ https://t.co/foYhINcBwO pic.twitter.com/zh1mzbih5R
Internal fraud
Internal fraud is defined as intentional deception or concealment for the purpose of personal financial gain by malicious employees. All departments of the company can be concerned: accounting and payroll, financial management, purchasing, sales...
Three questions to Jean-Marc Mongredin, Deputy Director of Accounting at Ellisphere
How does Ellisphere manage the risk of fraud on a daily basis?
First of all, all employees of our finance department are aware of the risks of fraud. They are regularly informed and made aware of the different fraud techniques used. On a daily basis, we rely on written procedures and digitalized validation workflows.
In concrete terms, what actions have been put in place to manage this risk?
The key is awareness and common sense. Above all, it is important not to make any changes without first validating them, especially not if the request comes from a simple phone call, an email or a letter. In this case, a procedure is required. You must call the requester with a clearly identified internal contact (the buyer who knows his supplier, the salesperson who follows his customer, etc.) in order to certify any request that seems sensitive.
In the case of fraud against the president, for example, our existing processes make this risk of fraud almost impossible. In the event of such a call or request, we must take the initiative to systematically and directly call back our president to remind him of our rules. In case of proven fraud, we will report the incident to our legal department.
Our second axis of the fight against fraud focuses on a set of procedures with a strict separation of tasks for each employee.
- Procedures and workflows
We have written and implemented several operating procedures that describe the validation processes for each major family of financial flows. Everyone in our company knows that we cannot make any transfer (even extremely urgent ones) outside of our validation circuits where every change in sensitive data must be approved.
We have a procedure to follow to validate all the control points until a transfer is executed. On a daily basis, all accounting and financial flow requests must incorporate our acceptance circuits (for purchases, customer invoices and credit note requests, expense reports, etc.) with digitized validation workflows that begin with the initial request and end with the final payment for a supplier or the sending of an invoice or a customer credit note after validation of an order and deposit in a contract database
- Functional separations
The separation of functions in our company means that people who make transfers have no authority to change IBANs or make purchases, or to integrate documents other than bank documents. Let's take the example of our purchase invoices, any request must be the subject of an order. This request, validated by an authorized person, will be reconciled with the digital invoice which will itself be verified (address, entity, IBAN) by the supplier's accounting department.
A payment voucher from an authorized buyer will allow the payment circuit to be integrated. The payment circuit is managed by the treasury department which will also make these verifications and put the invoices in payment. Finally, the transfer file will be confirmed by the highly secure EBICTS banking system with two authorized signatories who have specially designed keys with a double electronic signature. It should also be noted that the implementation of dematerialized flows, as well as the electronic signature, reduces the risk of fraud with the strong identification of the right company and the right interlocutor.
Has the Covid-19 crisis increased the risk of fraud at Ellisphere?
As soon as a crisis arrives and takes hold, cyber attacks tend to escalate. In addition, with remote teams, we have seen the number of malicious emails, such as ransomware or requests to change IBR or entity, increase. However, even if the risk of fraud can increase, I don't think there is any more risk in a telecommuting situation than in a face-to-face one.
It is always necessary to raise awareness about fraud. Make sure to be informed about new hacking techniques that are constantly evolving and above all validate with whom we work, approve the documents that are necessary for the execution of our function and certify the proper conduct of operations.
In the future, we will certainly have to go even further by simulating cases of fraud to test our models and adapt them, as is the case for our IT department, which sends out fake emails to test the reaction of employees and thus measure their maturity in fraud risk management.